How unified kill chain works | complete guide for beginners
you can consider the unified kill chain as an updated and most reliable version of cyber kill chain (traditional threat model for defending against cyber attacks). This model covers most of the attack vectors and effective against advance persistence threats (APTs) and ransomwares.
“kill chain” is a military term used to describe series of steps attackers follow up in order to attack their target. In cybersecurity, the approach is adopted by cyber threat actors to perform a successful cyber attack in order to achieve their goals.
Phases and Steps of unified kill chain
The model consist of 16 steps and 3 phases (In, Through, and Out). Each phase has multiple steps in accordance with intentions and objectives of threat actors.
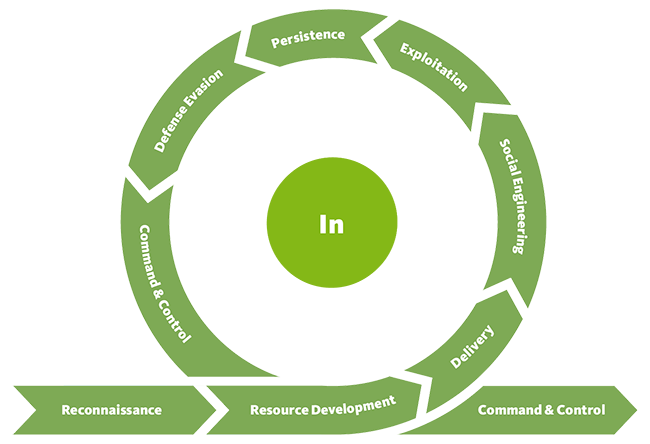
In (First Phase)
“opening the door by some means or climbing the wall in order to enter the building”. Threat actors try to breach the target’s perimeters in order to gain initial access which is main objective at the first phase. The phase consist of following steps:
Reconnaissance
In the Reconnaissance step of the Unified Kill Chain, an attacker gathers information about a target organization. For example, an attacker researching a financial institution might scour social media and LinkedIn to identify key employees and their roles.
They might also examine the institution’s website for details about its infrastructure and security practices. This collected information helps the attacker craft personalized phishing emails or identify potential vulnerabilities to exploit, increasing their chances of successfully breaching the organization’s defenses.
Resource development
In the Resource Development step of the Unified Kill Chain, an attacker prepares tools and infrastructure for the attack. For instance, they might create a malicious website that mimics a legitimate financial service, set up command and control (C2) servers to manage the attack, and develop malware specifically designed to exploit known vulnerabilities.
These resources are then used in later phases to deliver the attack payload, maintain control over compromised systems, and achieve their ultimate objectives.
Delivery
In the Delivery step of the Unified Kill Chain, an attacker transmits a weaponized object to the target. For example, an attacker might send a spear-phishing email to an employee of a financial institution.
The email contains an attachment disguised as an important document, which actually holds malicious code. When the employee opens the attachment, the code is executed, allowing the attacker to establish a foothold in the target’s network, setting the stage for further exploitation.
Social Engineering
In the Social Engineering step of the Unified Kill Chain, an attacker manipulates individuals to perform actions that compromise security. For example, an attacker might call an employee of a financial institution, posing as IT support.
They inform the employee of a fake urgent security update and instruct them to visit a specific website to download the update. Trusting the caller, the employee complies, unknowingly downloading malware. This malware grants the attacker access to the organization’s network, bypassing security measures through the manipulation of human behavior.
Exploitation
In the Exploitation step of the Unified Kill Chain, an attacker takes advantage of a vulnerability to execute malicious code on a target system. For instance, an attacker might exploit an unpatched software vulnerability in a company’s web server. By sending specially crafted requests, they exploit the vulnerability to gain unauthorized access.
This allows them to install malware or open a backdoor into the system. Through this exploit, the attacker gains control over the server, setting the stage for further actions such as data exfiltration or network propagation.
Persistence
In the Persistence step of the Unified Kill Chain, an attacker ensures continued access to a compromised system. For example, after gaining initial access to a financial institution’s network, the attacker installs a backdoor or a rootkit on a key server.
This backdoor allows the attacker to regain access even if the initial entry point is discovered and closed. Additionally, they may create new user accounts with administrative privileges or modify existing ones, ensuring they can maintain control and continue their malicious activities without immediate detection.
Command and control
In the Command and Control (C2) step of the Unified Kill Chain, an attacker establishes a communication channel with the compromised system. For example, after infecting a financial institution’s server with malware, the attacker configures the malware to connect to a remote C2 server they control.
This connection allows the attacker to send commands, receive data, and remotely manage the compromised system. Through this channel, they can execute further actions, such as data exfiltration or deploying additional malicious tools, maintaining control and coordination over the ongoing attack.
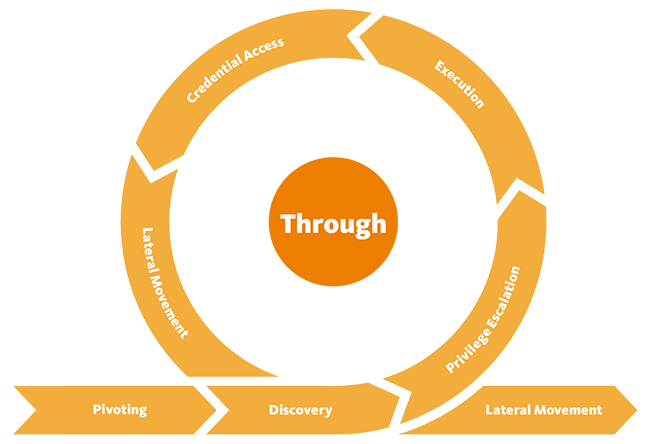
Through (Second Phase)
Searching every corner of the building in order to find an easiest way to steal most precious items. After gaining the initial access, the threat actor dive deep into the network system of the target in order to escalate privilege and avoid detection. The phase consist of following steps:
Pivoting
In the Unified Kill Chain, “Pivoting” refers to the technique where an attacker uses a compromised system as a stepping stone to access other systems within the same network or across different networks. For example, after gaining initial access to a low-security server in a financial institution, the attacker discovers it has connections to more critical systems like a database server.
They exploit vulnerabilities in the low-security server to pivot into the database server, allowing them to steal sensitive customer information or manipulate financial records, expanding their control and impact within the organization.
Discovery
In the Discovery step of the Unified Kill Chain, an attacker actively explores the compromised network to gather information about its structure, resources, and potential vulnerabilities. For instance, after infiltrating a financial institution’s network, the attacker uses scanning tools to identify all connected devices, such as servers, workstations, and network devices.
They analyze the network topology and map out critical assets like databases or payment systems. This reconnaissance helps them prioritize targets for further exploitation, understand the network’s defenses, and plan the next steps in their attack to maximize their impact and achieve their objectives.
Privilege Escalation
In the Privilege Escalation step of the Unified Kill Chain, an attacker increases their level of access within a compromised system or network. For example, after gaining initial access to a financial institution’s server with limited privileges, the attacker exploits software vulnerabilities or misconfigurations to gain administrative rights.
With elevated privileges, they can bypass security controls, install more sophisticated malware, access sensitive data, or manipulate critical systems without being detected. Privilege escalation allows attackers to deepen their foothold in the network, expanding their capabilities and potentially causing more significant damage or achieving their malicious objectives effectively.
Execution
In the Execution step of the Unified Kill Chain, an attacker initiates the main objective of their cyber attack. For instance, after gaining access to a financial institution’s network through phishing and reconnaissance, the attacker deploys ransomware across critical servers and workstations. This malicious software encrypts sensitive data, rendering it inaccessible to the organization.
The attacker then demands payment in cryptocurrency for decryption, exploiting the institution’s urgency to restore access to critical systems. Execution marks the culmination of the attacker’s efforts, where they achieve their primary goal, whether it’s data theft, system disruption, or financial extortion.
Credential Access
In the Credential Access step of the Unified Kill Chain, an attacker aims to obtain valid credentials that grant them unauthorized access to systems or resources within a target network. For example, after infiltrating a financial institution’s network through a phishing attack, the attacker uses tools like Mimikatz to extract plaintext passwords from memory or capture hashed credentials stored on compromised systems.
With these credentials, they can authenticate themselves as legitimate users or administrators, bypassing initial security measures and gaining extensive control over critical systems, enabling further exploitation, data exfiltration, or deeper network penetration.
Lateral Movement
In the Lateral Movement step of the Unified Kill Chain, an attacker navigates through a compromised network to expand their reach and access additional systems or resources. For example, after gaining initial entry into a financial institution’s network through a phishing attack, the attacker uses stolen credentials to move laterally from an infected workstation to a file server.
They exploit vulnerabilities in poorly secured network segments or weakly protected systems to escalate privileges and gain access to critical databases containing sensitive financial data. Lateral movement allows attackers to spread their influence across the network, increasing their potential impact and control over valuable assets.
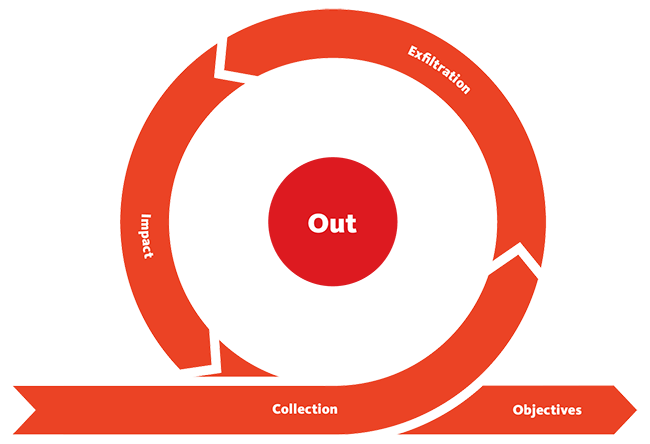
Out (Third phase)
Stealing the precious items of the building and exit it without any interruption. The threat actor after compromising the target, trying to achieve its final objectives (encrypting file for ransom or exfiltrating sensitive data). The phase consist of following steps:
Collection
In the Collection step of the Unified Kill Chain, an attacker gathers valuable information or data from compromised systems within a targeted network. For instance, after gaining access to a financial institution’s database server through credential theft and lateral movement, the attacker identifies and extracts customer payment card information stored in a specific database.
They use automated tools to systematically retrieve large volumes of sensitive data, which they then exfiltrate to their external servers for exploitation or resale on the dark web. Collection allows attackers to achieve their objectives by acquiring critical information that can be monetized or used for further malicious activities.
Exfiltration
In the Exfiltration step of the Unified Kill Chain, an attacker transfers stolen data from a compromised network to an external location under their control. For example, after successfully collecting sensitive financial data from a bank’s database through advanced malware and credential theft, the attacker encrypts the data and sends it in small, unnoticed chunks to a remote server outside the bank’s network.
This data could include customer information, transaction records, or proprietary business data. Exfiltration allows attackers to profit from or exploit stolen information while avoiding detection and maintaining control over the compromised network.
Impact
In the Impact step of the Unified Kill Chain, an attacker achieves their ultimate goal, causing significant harm to the targeted organization or its stakeholders. For instance, after successfully exfiltrating sensitive financial data from a bank’s network, the attacker publicly releases the information. This action damages the bank’s reputation, leading to a loss of customer trust and regulatory penalties.
Additionally, the exposure of confidential data may result in financial fraud or identity theft affecting customers. The Impact phase underscores the destructive consequences of a cyber attack, demonstrating the attacker’s ability to achieve lasting and detrimental effects on their target.
Objectives
n the Objectives step of the Unified Kill Chain, an attacker fulfills their strategic goals through the successful execution of their cyber attack. For example, after breaching a financial institution’s network through sophisticated phishing and malware tactics, the attacker’s objective might be to disrupt financial transactions.
They achieve this by manipulating transaction records or temporarily disabling critical banking services, causing financial losses and customer inconvenience. The Objectives phase reflects the attacker’s ultimate intention behind their actions, whether it’s financial gain, sabotage, espionage, or other malicious motives, demonstrating the impact and strategic intent of their cyber operation.
Closing Thoughts
Understanding the Unified Kill Chain provides crucial insights into the intricate stages of a cyber attack. From initial reconnaissance and resource development to the execution of objectives and the eventual impact, each phase illustrates how attackers methodically exploit vulnerabilities to achieve their goals.
By comprehending these steps, beginners can grasp the complexity and severity of modern cyber threats, empowering them to enhance their cybersecurity practices. Awareness of the Unified Kill Chain not only aids in threat detection and mitigation but also underscores the importance of proactive defense measures and ongoing vigilance in safeguarding digital assets against evolving threats.





